Every job is a self-portrait of the person who did it. Autograph your work with quality.
Happy New Year!
This is amazing! January 2024 is my 40th year of business anniversary! It’s been a long and exciting ride. Here’s a recap:
1984: Compaq Portable, advertised as the first 100% IBM PC-compatible computer was introduced. Compaq recorded first year sales of $111 million, the most ever by an American Business in a single year. And YES, I have one. It was my first computer!
1985: The Compaq Deskpro 386 is introduced. DOS 3.2 announced. I say “I DO” to the question: Until death do you part? I also figure out that no where in those vows did I promise to not be the cause of his death! He has been cautiously fulfilling his vows!
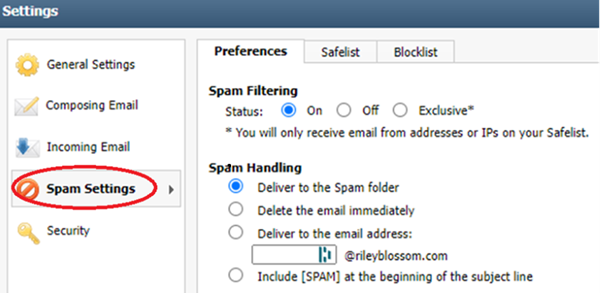
1987: Comp-U-Talk rents its first commercial location. Some of you may remember our office on Broadway in Coos Bay.
1989: Intel introduces the 80486 microprocessor. Affectionately referred to as “486”. Google is founded.
1990: Windows 3.0 and Microsoft Solitaire Debut. Tim Berners-Lee writes the first website. See it here: http://info.cern.ch/hypertext/WWW/TheProject.html. Our family size increases. Baby Robin comes to work.
1994: Nothing notable happening in the computer arena. Baby Sara joins our family.
1995: Windows 95 appears
1998: Windows 98 released
1999: Y2K panic is everywhere. I birth a Y2K compliant baby!

2000: Windows ME is introduced
2001: Windows XP replaces the shoddy Windows ME
2007: Windows Vista—are you kidding? This isn’t good!
2009: Windows 7—YEAH! Finally, an Operating System that Operates!
2011: I consider changing my name to “Charity”. The IBM computer named Watson is going to play Jeopardy against Ken Jennings and Brad Rutter. If the computer wins, IBM will donate 1 million to “Charity”. The complete story can be found here:
2012: Windows 8, Another shoddy attempt
2014: Windows 10 introduced. Microsoft gives it to Windows 8 users.
2017: My love of chickens and a bout of flu intersect with a newsletter: When you find yourself in danger, When you’re threatened by a stranger, When it looks like you will take a lickin’, There is someone waiting, Who will hurry up and rescue you, Just Call for Super Chicken!

In case you have never heard the Superchicken theme song (it was part of the animated TV series, George of the Jungle back in the 60’s) you can play it here: https://youtu.be/FKss2pBYQ6Y . If you can sing it to us when you drop off the computer for repair we will discount your service $10.
2021: Windows 10 becomes Windows 11.
2024: Looking forward to more adventures.
Stay Safe, Stay Healthy, Stay in Touch!!
Janet