“There are only two types of companies: those that have been hacked, and those that will be.”
Robert Mueller, FBI Director, 2012
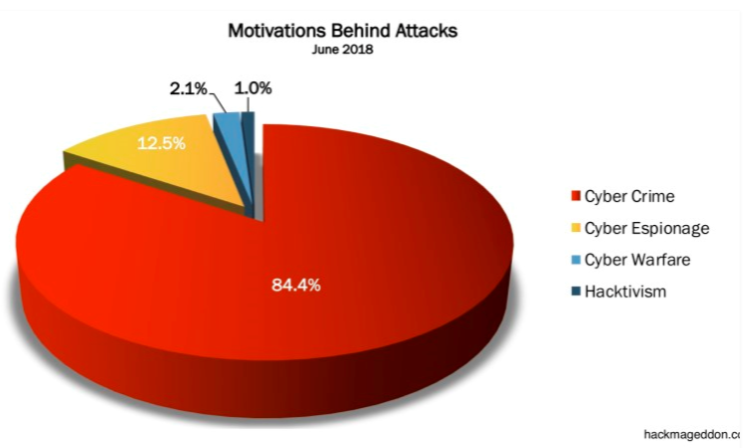 Cyber Crime: criminal activity or a crime that involves the Internet, a computer system, or computer technology: identity theft, phishing (dictionary.com)
Cyber Crime: criminal activity or a crime that involves the Internet, a computer system, or computer technology: identity theft, phishing (dictionary.com)
Cyber Espionage: a form of cyber attack that steals classified, sensitive data or intellectual property to gain an advantage over a competitive company or government entity: Russians influencing the election, spying on the DNC. (carbonblack.com)
Cyber Warfare: virtual conflict initiated as a politically motivated attack on an enemy’s computer and information systems. Attacks disable financial and organizational systems by stealing or altering classified data. (techopedia.com)
Hacktivism: the practice of gaining unauthorized access to a computer system and carrying out various disruptive actions as a means of achieving political or social goals: a hacker tries to alter or deface a website. (dictionary.com)
The following statistics are from https://www.comparitech.com/vpn/cybersecurity-cyber-crime-statistics-facts-trends/ & https://www.comparitech.com/identity-theft-protection/identity-theft-statistics/
- An attacker resides within a network for an average 146 days before detection.
- A University of Maryland study found that hackers are attacking computers and networks at a “near-constant rate”, with an average of one attack every 39 seconds.
- 43 percent of cyber attacks against businesses worldwide target small companies.
- According to a CSID survey, 52% of small businesses don’t invest in cyber risk mitigation, believing that they don’t store any private information. However, 68% at a minimum store email addresses, which is one potential entry vector for hackers.
Worried about your security? We have tools. We can help.
Keeping Your Data Safe!
~Janet
