Fun Fact: The number of exclamation points now necessary to convey genuine enthusiasm online is, according to most internet users, three!!! ~ https://tinyurl.com/y9a53w42
Thirty-five years ago, I was faced with a decision: Unemployment or Self-Employment? Both options were terrifying! So, I made a deal with God. I promised to be self-employed but God had to keep the bills paid. I’m pleased to announce: 35 years of bills have been faithfully paid.
Lots of things have changed over the past 35 years. I still remember my mentor telling me he would never outgrow a 10 Meg Hard Drive. That still makes me smile. I frequently get calls from people in distress because the file they are trying to email is larger than 10 Meg and their email provider has a 5 Meg limit.
Computers are much smaller and much faster and much more fun than they were 35 years ago. My first computer was a portable, although calling it a luggable was much more appropriate. It had 2-5.25” floppy disk drives, no hard drive and weighed about 30 pounds. The screen had awesome green characters on a black background; No horrible amber letters for me!
Today I carry a computer in my back pocket. It has a 5” screen, weighs less than a pound and lets me make phone calls, read email, look up stuff on the internet and play games.
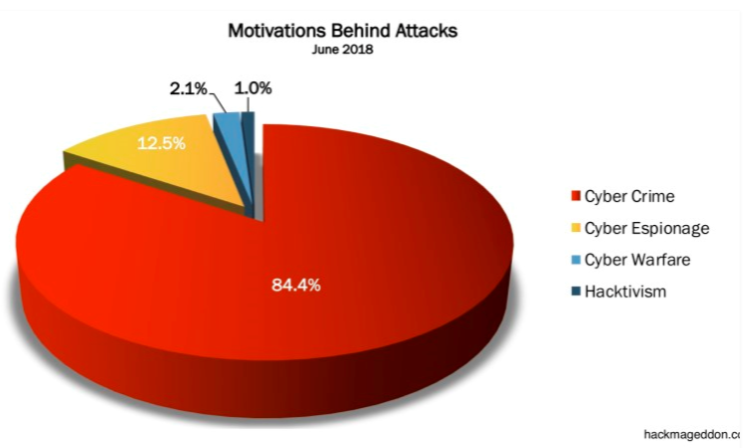
Technology has made significant changes over the years. Unfortunately, not all of them have been good. It doesn’t much matter if you talk computer technology, medical technology, advancements in transportation, or even education. Whenever something good comes along, there will be some small segment who will figure out a way to use the good for something evil. Computing is no different. 2018 saw it’s share of bad via data breaches.
In November, Marriott announced that as many as 500 million people were affected by a data breach. In September, Face book announced it had accidently shared 30 million users’ data. The City of Atlanta was crippled by ransomware in March. Russian hackers launched cyberattacks on the Olympics in February. And in October, our beloved Google admitted to exposing the data of 500,000 users of Google+. https://tinyurl.com/y7a8kyf4
What’s a discerning computer user to do? Chances are, your data has been exposed. You can verify here: https://haveibeenpwned.com/. If your data has been breached, I highly recommend changing passwords for the breached accounts. If you are responsible for others’ data, i.e. customers, vendors, employees, a good firewall is imperative. Employee education is highly recommended and affordable. Our colleagues at KnowBe4.com report that email is still the #1 attack method. They say 92% of malware is delivered by mail. https://tinyurl.com/y6wo6hft You don’t want to be the cause of a data breach. If you would like personal training, let me know. I’m considering putting together an official class. I will add your name to my list.
Are you interested in seeing a more comprehensive list of data breaches? Check out: https://en.wikipedia.org/wiki/List_of_data_breaches
Until Next Month, Happy New Year and remember to
Keep Your Data Safe!